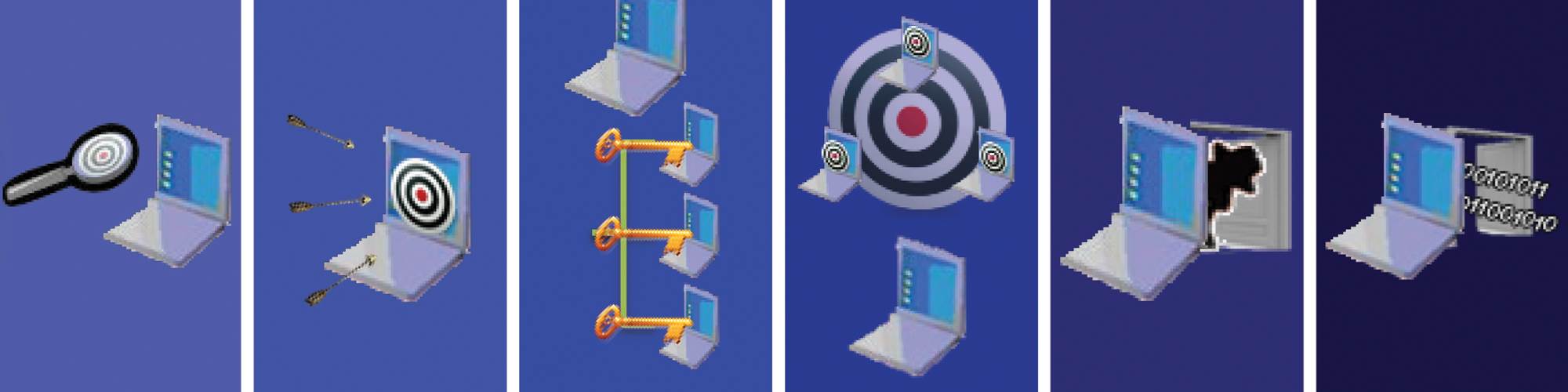
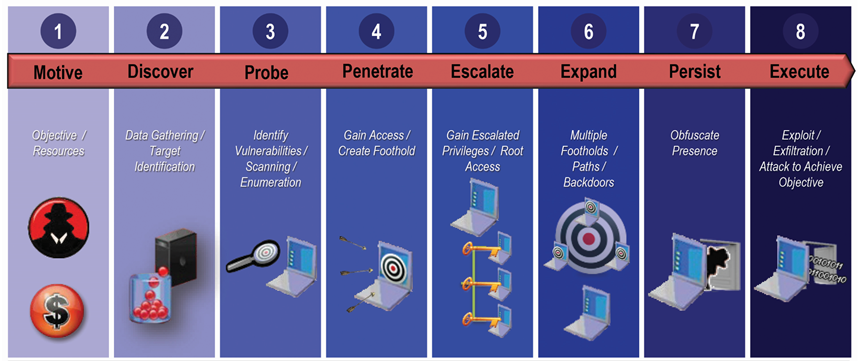
Traditional manufacturing focuses on the act of converting raw materials into finished products by using manual or mechanized transformational techniques, whereas advanced manufacturing focuses on the use of technology to improve products and processes. In the mid-1960s, American manufacturing was still separated into these two categories: hard product industries vs. manufacturing process technologies. Detroit was traditional manufacturing; Silicon Valley was advanced manufacturing.
Now, to the extent possible, all manufacturing is moving away from a traditional orientation to an advanced one. U.S. manufacturing today is characterized increasingly by automation, interconnectivity, sensors and RFID chips, artificial intelligence, cyber-physical production systems and the Internet of Things, and discussions around smart manufacturing, or industry 4.0 and smart factories. We are in the fourth industrial revolution.
Why go after a small to mid-size business like a mold builder? The answer is simple: mold builders represent an easier target to penetrate and do so successfully.
cybersecurity in moldmaking
Cybercrime in Moldmaking
What does this transformation mean when it comes to cybersecurity? And what does it mean for the plastics industry and moldmakers, specifically? Given its focus on innovation and an increasing reliance on connected products, the manufacturing industry is particularly vulnerable to cyber risks.
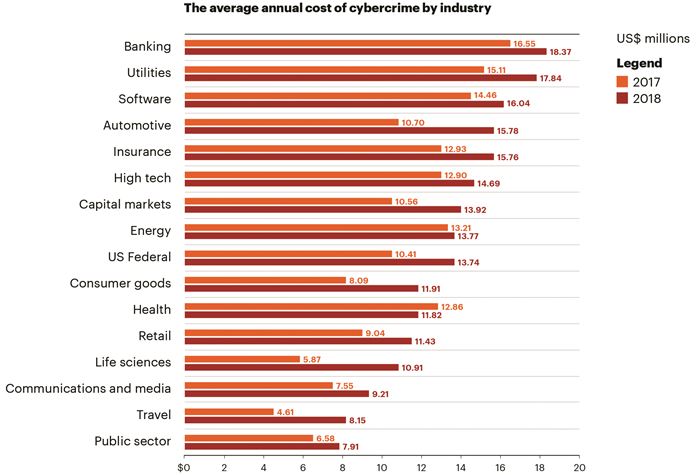
Manufacturing was one of the top five most targeted industries in 2016, 2017 and 2018. Cybercriminals are increasingly targeting small- and medium-sized businesses. In 2018, 67% of small- and medium-sized businesses experienced a cyberattack, and 58% experienced a data breach in the last 12 months.
Not only are cyberattacks on small- and medium-sized businesses rising, but more are experiencing highly sophisticated and targeted cyber attacks, exposing them to serious cybercriminals, according to 2018 State of Cybersecurity in Small and Medium Size Businesses study, conducted by Ponemon Institute and sponsored by Keeper Security.
Why go after a small- and medium-sized businesses like a mold builder? The answer is simple: mold builders represent an easier target to penetrate and do so successfully. With larger businesses might come larger rewards, but these companies also have larger budgets and, in many cases, a greater awareness of the threat and their vulnerabilities.
Regardless of the size of your business, cybercriminals seek access to your network and will take advantage of any vulnerability. A single unprotected or improperly secured device can be all that is needed to access your entire system.
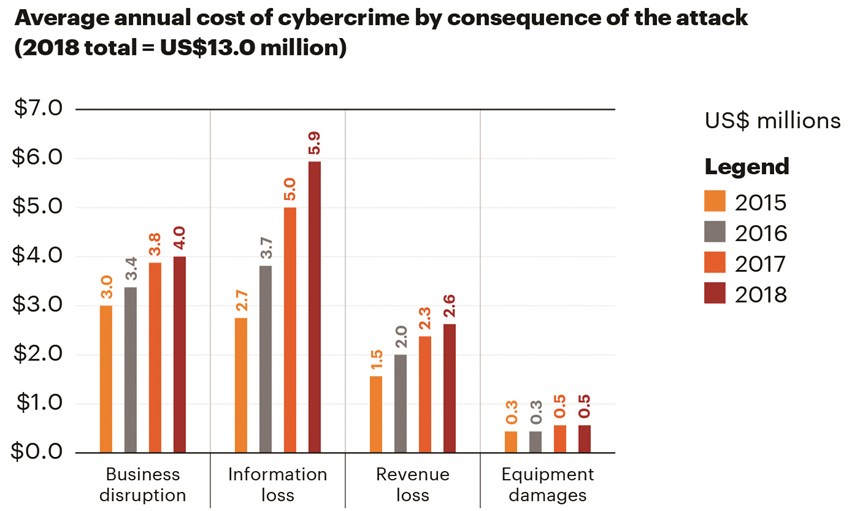
When a cybercriminal attacks a multinational or global company, the cost can be astronomical whereas, the average cost for small businesses to clean up after being hacked is about $690,000, and, for middle-market companies, it is over $1 million, according to Ponemon Institute study.
This may seem insignificant when compared to the high-profile cases that end up in the news, but these costs represent a huge financial burden for a small- and medium-sized business. In fact, 60% of small companies are unable to sustain their business more than six months following a cyberattack, according to “Internet Privacy in the Digital Age” by Champlain College, Graduate Studies.
These businesses frequently do not have adequate resources to deal with the impacts and aftermath of a cyberattack. Keep in mind the smaller your business, the more vital it is to protect your data, your intellectual property, your trade secrets and all your assets.
Given its focus on innovation and an increasing reliance on connected products, the manufacturing industry is particularly vulnerable to cyber risks.
A Cybersecurity Plan
The question is not if you will experience a successful cyberattack but when. Here is what you do about cybersecurity to address your shop’s vulnerabilities.
- Educate yourself and educate your employees, make cybersecurity a priority, a part of your business culture and operations.
- Conduct an inventory of your vulnerabilities, performing what is often called a threat assessment.
- Take steps to address your vulnerabilities.
Here are some simple examples of things that can make you a harder target to attack include:
Implement a secure password management solution to address common weaknesses like a failure to use strong passwords, two-factor authentication and unique passwords for every website, application and system.
Use network systems that include ways to encrypt data, authenticate users and authorize access.
Consider policies addressing the behavior of your employees. Remember, 48% of data security breaches are caused by acts of malicious intent; however, human error or system failure represents the remainder. Examples include eliminating non-business uses of devices on-site or forbid the use of any plug-in devices like USB flash drives.
Keep in mind how physical security interfaces with your ICT security. An issue of concern here is making sure former employees have their access to systems, whether it be on-site or remote, locked out immediately doing whatever might be required here. For example, changing passwords, confiscating ID badges, entry fobs, etc.
Evaluate and implement other risk mitigation steps, like regularly upgrading software solutions and monitoring business credit reports. A study has found that it takes an average of 193 days before a patch gets applied to fix a problem, even though the patch is available, according to the BMC Tech Dossier: SecOps Solutions Help Teams Address Critical Security Vulnerabilities.
A single unprotected or improperly secured device can be all that is needed to access your entire system.
Also, remember that an ever-growing number of well-known off-the-shelf software programs contain malware, so if possible, consider adopting customized software solutions for your use.
Discuss cybersecurity with your suppliers and customers or anyone who interconnects with your network and systems. Determine how cybersecure and aware they are.
These are just some of the steps you can take and not intended to be all-encompassing, but any response from you will require a cybersecurity strategy and some budgeted resources. In conclusion, remember that you cannot make yourself invulnerable here, so you need to plan on how to respond when a cyber attack occurs. You need to plan on how to get your people, processes and technology back up and running as quickly as possible.
Related Content
The Trifecta of Competitive Toolmaking
Process, technology and people form the foundations of the business philosophy in place at Eifel Mold & Engineering.
Read MoreThe Role of Social Media in Manufacturing
Charles Daniels CFO of Wepco Plastics shares insights on the role of social media in manufacturing, how to improve the “business” side of a small mold shop and continually developing culture.
Read MoreMold Builder Uses Counter-Intuitive Approach for Mold Challenges
Matrix Tool Inc. answers customers’ hard questions with creative solutions for cavity spacing, tool sizing, runner layout and melt delivery that reveal the benefits of running in a smaller press size at lower cavitation but higher yield.
Read MoreMold Design Review: The Complete Checklist
Gerardo (Jerry) Miranda III, former global tooling manager for Oakley sunglasses, reshares his complete mold design checklist, an essential part of the product time and cost-to-market process.
Read MoreRead Next
Cybersecurity Requires a Culture Change
The industry talks a lot about culture change, but I’m almost certain they are not referring to cybersecurity. I’m even more certain that most shops do not have a dedicated IT person focused on cybersecurity. Meet Eric Slaughter.
Read MoreA Q&A on Cybersecurity with Paragon D&E
Cybersecurity continues to be a critical issue for manufacturers, and after touring Paragon D&E a while back I knew they had things in order. So, I reached out to President David Muir to see how they handle cyber threats.
Read MoreReasons to Use Fiber Lasers for Mold Cleaning
Fiber lasers offer a simplicity, speed, control and portability, minimizing mold cleaning risks.
Read More